Wazuh
Wazuh is the SIEM software that is used to make sure that all of our computers are up to standard in terms of system health and to monitor any security events. The Wazuh server lives on Valhalla in an Ubuntu virtual machine called McGill which is named after Chuck McGill from Better Call Saul. The previous Wazuh server which was replaced due to instability was called Gustavo which was named after the manager of Los Pollos Hermanos and a kingpin in a criminal syndicate in the television series Breaking Bad. There are also agents that are deployed onto each device which collect necessary information that will be needed to make a full report on any issues that may be occurring on said system. All of the data is then processed and sent to the manager which takes all of the data and organizes it into one source. It also utilizes Elasticstack which visualizes all of the data the manager has so that everything going on in 24Pintech's systems can be monitored without much hassle.
ㅤ
Configuring Wazuh Agents
Installation Process
Wazuh Agent Windows Configuration
If you need to the Wazuh agent can be downloaded from https://documentation.wazuh.com/current/installation-guide
- Get Wazuh running on a computer that already has it installed
- Open command prompt (admin)
- Run the command below
"C:\Program Files (x86)\ossec-agent\agent-auth.exe" -m 10.21.25.12 -P password- If this command worked you are done. If this command fails you need to remove the agent from the list.
- Get Wazuh running on a 24pintech computer that does not have it installed
- In file explorer navigate to Cisco Curriculum (P:) in this PC
- Copy the Deployed Applications folder and paste it in C:
- (NOTE) If the computer doesn't have Cisco Curriculum (P:) you will have to get a thumbdrive with the file Deployed Applications
- Change the folder name to DeployedApplications
- Run Windows PowerShell as ADMIN
- Enter:
cd c:\DeployedApplications - Enter the command:
.\wazuh-agent-4.4.1-1.msi /q WAZUH_MANAGER="10.21.25.12" WAZUH_REGISTRATION_SERVER="10.21.25.12" WAZUH_REGISTRATION_PASSWORD="password" - Make sure that your command has the same version of Wazuh as the Wazuh Agent in DeployedApplications
Wazuh Agent Mac Configuration
- Log in to the computer with the 24pintech account. You may also open this wiki page on that computer to copy and paste commands.
- Open a terminal window and install Wazuh agent using this command:
curl -so wazuh-agent-4.3.9.pkg https://packages.wazuh.com/4.x/macos/wazuh-agent-4.3.9-1.pkg && sudo launchctl setenv WAZUH_MANAGER '10.21.25.12' && sudo installer -pkg ./wazuh-agent-4.3.9.pkg -target /(If prompted, use the 24pintech account password to finish the installation) - Run this command to start Wazuh:
sudo /Library/Ossec/bin/wazuh-control start - Verify that the agent has been added in wazuh after refreshing the page.
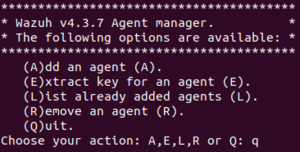
Wazuh Agent Manager
Running this command will open the menu to add, remove, and edit agents (see picture on the right)
/var/ossec/bin/manage_agents
- Add an agent (A)
By entering "A" you can add an agent to the list. All you need is to input the name of the computer you want to add and the computers IP address.
- Extract key for an agent (E)
By entering "E" you can get a new key for an agent. All you need is to input the ID number of the agent. This can be done to help get a new key however this is likely unnecessary as you just need to run one command from command prompt on the agent you are trying to give a key to. (See "Wazuh Agent Windows Configuration")
- List already added agents (L)
By entering "L" you can view a list of every agent and that agents ID number. This can also be viewed from the Wazuh manager page in more detail however this is often a very convenient command when you need to check the list for one agent.
- Remove an agent (R)
By entering "R" you can remove an agent from the manager by entering the agents ID number. This is useful to remove agents we do not need or to remove faulty agents to fix them and get them running properly.
- Quit (Q)
By entering "Q" or alternatively "Quagmire" you can close the menu and return to the normal terminal screen.
Monitoring Wazuh
How to Monitor
There is a lot of information present on the manager page with details on everything connected. Mainly, all the information that will want to be looked at is present on the Security Events, Integrity Monitoring, Agents, and Manager tabs for the information that we will be troubleshooting and coming up with solutions for. The main thing that will need to be looked for are going to be any failures seen on one of the servers or workstations. You will also want to look at the agents connected to see if things are in order or not with connection to the manager. Another thing would be vulnerabilities detected by the manager within our systems and note what kind of vulnerability that it is. The processes being made will also be something that needs to be monitored for any issues on the systems.
What to look for
Modules
Security information management
- Security Events
- Alerts - This will be the main place to look for all of the systems current events taking place as far back as you need to. This will go over any login failures, malware, or anything of that nature will be viewed here across all agents. The key to looking at this all is section through the level of alert going from 1 - 12 with each increase in level being a higher alert that needs to be looked at. Anything above 7 will typically be what is unwanted unless another technician is performing a task that is causing said alerts. Take the proper steps as listed within the policy when any alert is worth being taken to the higher ups for proper handling.
Auditing and Policy Monitoring
- Security Configuration Assessments
- Here will be the most important place to look as you will need to monitor for any faults detected in the system's security. One of each device (All servers need to be checked) and then you as a tech will need to research into the issue if it is important. If there is a major security issue then this can be dealt with either by informing a higher up and getting the all clear to fix it, or if you are already in charge of fixing the security of the systems.
Management
Administration
- This will probably be the most unused section of the SIEM, but if multiple technicians ever take it on then here is where all accounts would be managed depending on the trust within that technician, so restrictions can be set to ensure that all users have the correct access on the server, ensuring that nothing will be used against policy. This is also where rules will be configured for the nodes and clusters mainly for what will be showed on the virtual machine
Status and Reports
- This is where you will be able to generate a status report of the SIEM as well as seeing the status of each manager/cluster. By generating a report you will be given a detailed pdf of everything that has been logged for when you set it and you will be able to go over it and see anything that sticks out instead of having to check each individual module on the SIEM. You will also view the cluster health by seeing if one of the nodes has gone down and needs to be repaired to get it in working order once more.
Agent
- Any and all issues that are had within the agent monitoring page can be checked for in the troubleshooting section of the SIEM: Configuration wiki page.
Active
- Here you will be looking for any and all agents connected to the SIEM. You will look here for any newly added agents that are supposed to be there as well as if they have properly connected.
Disconnected
- You will look here to see if any important agents such as the servers are disconnected due to it being turned off or if it has been inactive for quite a while as they may need to be reset which can be done in many ways.
Never connected
- This will be used to check for any agents that have been connected improperly due to human error or any oversight that had happened during the configuration. If this happens to occur then some of the issues with the setup of an agent should be able to be fixed by viewing previous troubleshooting, but if the issue is unknown, then consult either the Wazuh documentation or a manager.
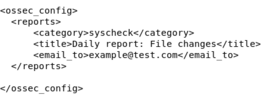
Reporting
Reports from the manager can be set up to email the information directly to us. In order to do this the Ossec.conf file needs to be edited to set up automatic reports by using the command With this you can choose who will receive it, the frequency of emails, and the level of alert it will send an email for once your information is filled into the box. Once you have made it in there will be a section to input a sending email and the recipient email, whatever your purpose is for receiving the email will most likely be for the higher alerts that need fixing immediately.
This is the command needed to access the ossec.conf file on the virtual machine.
sudo nano /var/ossec/etc/ossec.conf
Warning: Configuring the Ossec.Conf file on either of the nodes or the server web page can lead to the server malfunctioning. Make sure you know exactly what you are doing and you have a backup ready before changing anything.
Creating a new Wazuh Server
For whatever reason we may need to make a new Wazuh server. This could be due to the system breaking and we are unable to fix it or maybe the server starts to have problems over time and needs to be rebuilt to get rid of any bugs. Creating a new server sounds like it would be tough but it is actually ridiculously easy and simple. The steps for creating a new Wazuh server only consist of making a new VM running Ubuntu Linux and to run a handful of easy commands that do not require any Linux knowledge. After this all of the agents that were connected to the previous server will automatically transfer over to the new server.
Step 1: Create a new server
Create the new server in ESXi for Wazuh to run on. Note that you should have approval from a leader of the systems team or Chamberlain before you make a new server.
- First you need to name the server. All Wazuh servers are to be named after Breaking Bad/Better Call Saul characters. Currently we have already decided that if McGill ever needs to be replaced the server that fills its place should be named Schrader.
- Give it 4-8 CPU cores, 8 Gb of ram, and 250 Gb of storage.
- Put Desktop Ubuntu on the virtual machine. You will likely be using version 22.04 which is already on the 24PinTech shared storage however you should search and verify that this is still the recommended version of Linux. You should also use Desktop Ubuntu rather than Server Ubuntu because you lose a lot of functionality that is key to running Wazuh effectively if you use Server Ubuntu.
- Set up Linux on the image by simply going through the setup. Be sure to read what you are doing and do not just click through it.
Step 2: Install Wazuh
Note: You may open this wiki page on the server using Firefox and copy and paste commands instead of typing them manually.
- In a terminal window type this command:
sudo curl -sO https://packages.wazuh.com/4.4/wazuh-install.sh && sudo bash ./wazuh-install.sh -a - You will likely need to wait 5-15 minutes or potentially longer for this command to run. Just be patient.
Step 3: Change the password
- Enter this command:
sudo curl -so wazuh-passwords-tool.sh https://packages.wazuh.com/4.4/wazuh-passwords-tool.sh - Enter this command and change the text in the brackets to the chosen password:
sudo bash wazuh-passwords-tool.sh -u admin -p [PASSWORD]
Step 4: Change the IP
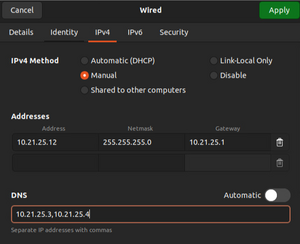
- Open the menu in the top right of the screen. Go to Wired Connected and then open Wired Settings. Click on the gear on the Connected option and go to IPv4.
- Set the IPv4 Method to Manual. You will now need to set the Address to "10.21.25.12". You must use this IP for all of the agents to automatically connect to your new server. Set the Netmask to "255.255.255.0". Set the gateway to "10.21.25.1". Set the DNS to "10.21.25.3, 10.21.25.4". To the right there is a picture of how the settings should look to use as a reference. Everything should be exactly the same. Once you are done hit Apply in the top right.
- On the previous screen turn Connected off and then back on. This should have applied the settings from last step.
Step 5: Verify Connectivity
- Go to the Wazuh servers web page. To access it enter https://10.21.25.12 into your search bar.
- For the username ender "admin" and for the password type in what you set the password as in step 3. You should now have access to the dashboard.
- Check to see if agents are connecting. If agents have connected you are done with the installation process and are now ready to begin monitoring.
Troubleshooting:
Type in the command sudo apt install net-tools and now enter the command ifconfig to see the IP. If the IP is anything besides 10.21.25.12 then you messed up in step 4. If necessary you can google a different tutorial in changing the IP online that may be more in depth.
Wazuh Commands:
Agent Config (Agent Side).
net stop wazuh- Stops Wazuh
net start wazuh- Starts Wazuh
Restart-Service -Name wazuhsystemctl restart wazuh-manager- Restarts Wazuh manager (This command sometimes entirely breaks Wazuh beyond repair. Be sure you have a snapshot before running this command)
"C:\Program Files (x86)\ossec-agent\agent-auth.exe" -m 10.21.25.12 -P password- Obtains a new key and activates an agent
Agent Config (Server Side)
/var/ossec/bin/manage_agents- Opens agent manager. More info on the manager under "Wazuh Agent Manager"
Server Config - Nano
systemctl start/status/stop/restart wazuh-manager/usr/share/kibana/data/wazuh/config/wazuh.yml/var/ossec/etc/shared/dbms/agent.conf/var/ossec/etc/ossec.conf/etc/filebeat/filebeat.yml/etc/kibana/kibana.yml/var/ossec/bin/wazuh-control -j info/var/ossec/logs/active-responses.log