Shield Security
To protect our website, we use a plugin called Shield Security. The plugin does everything from provide us real time audits, a log of all activity on our pages, forum spam, and more. As of 1.18.2023, we currently use the free version of the plugin. This means that the information on this site is tailored towards the free version and any features it may have in the future.
General
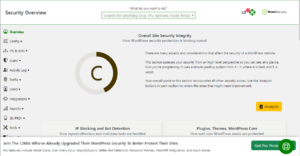
To access and modify the Shield Security plugin you will need to first navigate to the Shield Security menu, which can be found on the sidebar menu under the name "Shield Security." Clicking on the base menu option will bring you to the overview page or security dashboard as the submenu describes it. From this page you will be able to view the general letter grades that the plugin grants for general security concerns ranging from A+, which is the best score, to F, which is the worst. To get a quick overview on what to improve on to boost the letter grade, click on the Analysis button and a sidebar menu will open with details on how many points have been granted and what can be improved upon.
Reinstallation
In the case you ever have to reinstall Shield Security, the process is very simple and can be done in 3 steps. Before removing any plugin on WordPress you must deactivate it first. You will be able to find the option to deactivate the plugin on the Plugins menu under or beside the name of the plugin After deactivating the plugin you will now be able to delete the plugin. To delete the plugin, click on the delete button. If there are any prompts asking why you're deleting the plugin just click through them, it won't affect anything in the deletion process To add the plugin to the site, navigate to the Add New sub menu under the plugins. Make sure that you are in the add new menu before searching for the plugin, as the search menu in the base Plugin menu will only search through the installed plugins.
Config
The config menu compiles all of the specifics on each rule to be defined organized by different degrees of security benchmarks. Each category covers a specific aspect of the site, with the different categories come specific rules within their own subcategories, all spanning over the site going over different levels of website security.
IP Rules
The IP rules page holds a table of all offending IP addresses that try to breach our websites. The table holds their IP address, their status in concern to ability to connect to the site, the offence they committed, their last seen activity on the site, and the date of the offense.
Scans
The scans page holds an archive of the results of a recent scan done. The results of each scan are nestled under item specific tables according to where the scan took place and what it did or didn't find; with these tables being WordPress, Plugins, Themes, and Malware ( File locker is included in this list as well, however, it is a premium feature meaning that there is nothing we can utilize it for ).
Activity
Similar to the IP Rules page, the activity pages holds the catalogue of any changes done to the site by users or attempts to login by users. These attempts are labeled by severity, the IP of the user, the logged message of what they have done, and the date and time the event occurred.
Traffic
The traffic page shows an index of every http request made to the site, it shares a lot of similarity with the activity page as it chronicles about the same type of information however